


script description; last updated: October 14, 2004
| [scripts]
---------------------------------------------------------- The project
translates the white sovereign/naked bandit interdependencies into
a game with hierarchical process relations in the Unix kernel. The
kernel is the central element of the Unix operating system. It determines
the process and data organisation on which the other software elements
running under this operating system are based. 'Process' generally
refers to a program in execution. In order to initialise a process,
the kernel loads the program and assigns memory to it. Booting a computer
launches the init process. The init process, the highest hierarchical
status in the operating system, initiates a set of other processes.
All these follow-up processes descend from a parent process, i.e.
the cron descends from the init, the init is the parent of the cron,
the cron the child process from the init. Inside Unix, each process
can trigger a child process. There a two ways to terminate parent-child
relationships, and for both, Unix provides different scenarios: - a. If the child process is terminated before the parent, it will not be immediately removed from the kernel process list. First a signal will be sent to the parent in order for the deletion of the child to be confirmed. In the meantime, before confirmation, the child is in an intermediate status called 'zombie'. Zombies occupy memory in the process table, but are not effective anymore. - b. If the parent is terminated before the child, the child loses the parent and becomes an orphan process. The init process inherits the orphan, but the orphan stays in its origin process group level.   go to projectpage  go to krcf.org |
[scenarios
of misinformation and escape] ----------------------------- Starting
condition: the "white sovereign" is coded as the parent, the
"naked bandit" as the child process. |
scenario
A --------------------------------------------------------
- detailed processes: the script creates a variable "white_sovereign" (in which the whole script code is stored). The script exports this variable into the environment.
the script executes the white sovereign code.
 further information |
the
parent process creates a child process, which remains blocked in an
endless loop. The loop is sent into the background, the parent process
keeps waiting for the suspension of the child processes.
the code segment of the child process a) outputs its own script code (the one of the variable)
when this new code( sh clone.sh ) is executed, the child process can exit from the parent process relationship unnoticed, and becomes part of the init process. the script performs a camouflage - after its first execution it overwrites itself into its initial status on hard disc. the modified script: in this script, another process interface has been installed between parent process and child process.
|
the
clone:
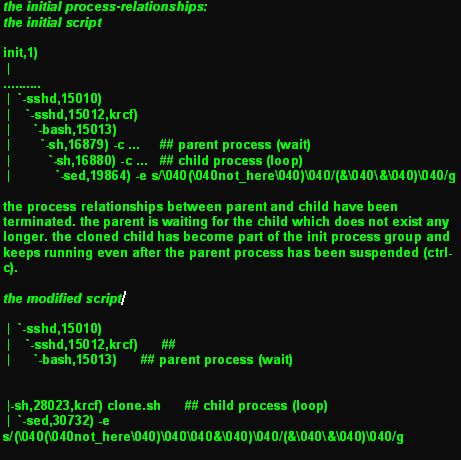
|
scenario
B --------------------------------------------------------In this
scenario, the shell script self-modifies during execution. Executing
the self-modified script, a child of the child is created. After this
creation, the child process terminates itself and sets free the child
of the child from white sovereign
dependency, in the same manner as described above. The child of the
child prints: "naked bandit: here, not here". During execution, the
self-modified script overwrites itself in the initial status.
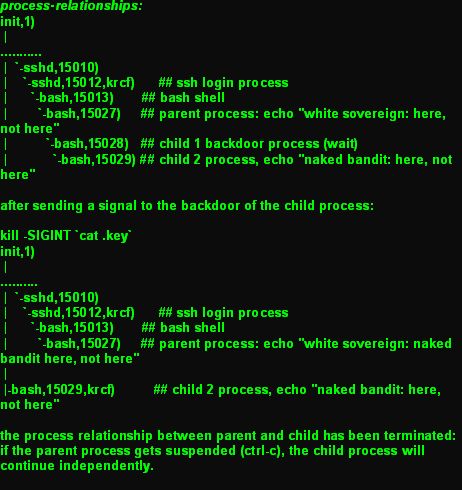
detailed processes: the script initiates a parent process (pid 15027), the parent process creates a child process (pid 15028) and sends it into background.
the child process (pid 15028) writes a secret key into a hidden file (.key),
the script forks from function "not_here" to function "here",
thus the child process forks again (pid 15029) and, unnoticed, creates an in-between process between the new child process and the parent process. ('unnoticed' since this splitting happens inside the child process) 
 go to projectpage  go to krcf.org |
the
new child (pid 15029) loops and prints out "naked bandit: here, not
here.
while [ enclosed ];do echo "naked bandit: here, not here";done; the parent process loops too and prints out "white sovereign: naked bandit here, not here".
|
|||||||||||||||||||
 |
|||||||||||||||||||||||||
|
|
|||||||||||||||||||||||||